Do you know what is scary about the stolen laptop of West Virginia-based Coplin Health Systems containing data of 43,000 patients? Or what’s bad in a contractor in Japan losing a USB drive having the personal information of 460,000 residents? The data wasn’t encrypted. So, a bad actor could easily access and sell personal data on the dark web. They learned the lesson the hard way. But that shouldn’t be the case knowing how easy it is to encrypt the data. The following sections discuss disk encryption, how to do it with BitLocker, and a few BitLocker alternatives.
Full Disk Encryption
Full Disk Encryption (FDE) refers to locking the drives to your system. It prevents access to the data on compromised devices and can allow for a boot-time check for additional security if applied on system drives.
BitLocker
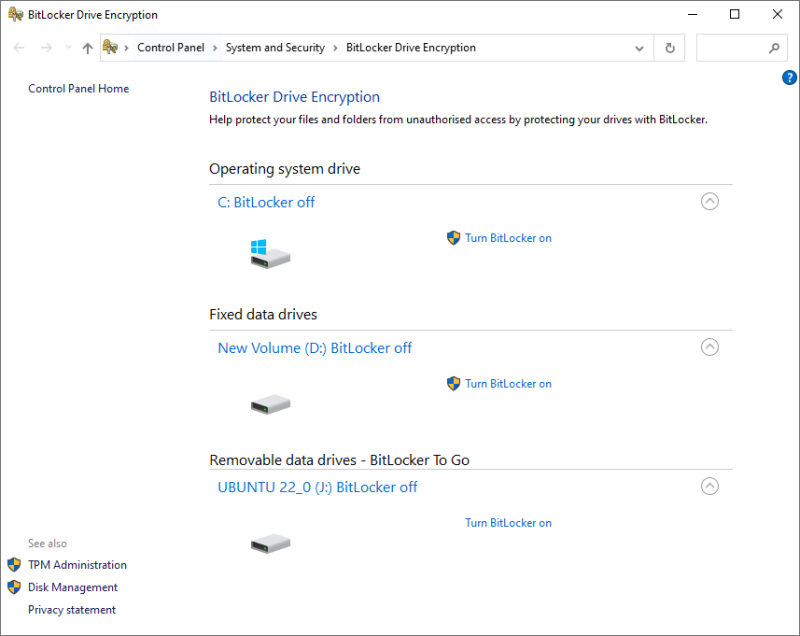
Windows professional, enterprise and education versions come preloaded with BitLocker device encryption. Using BitLocker, one can password-protect the drives, which function normally once you’re inside. There is also a recovery key to reset the password, without which the disk contents will be illegible. Besides, this works cross-platform. For instance, a drive encrypted on Windows will remain safe on Linux. To get started, type BitLocker in the taskbar search and open Manage BitLocker. Now choose the subject disk and click on Turn BitLocker on. The subsequent process is different for the operating system drive and non-system partitions, including portable disks.
BitLocker on System Drives
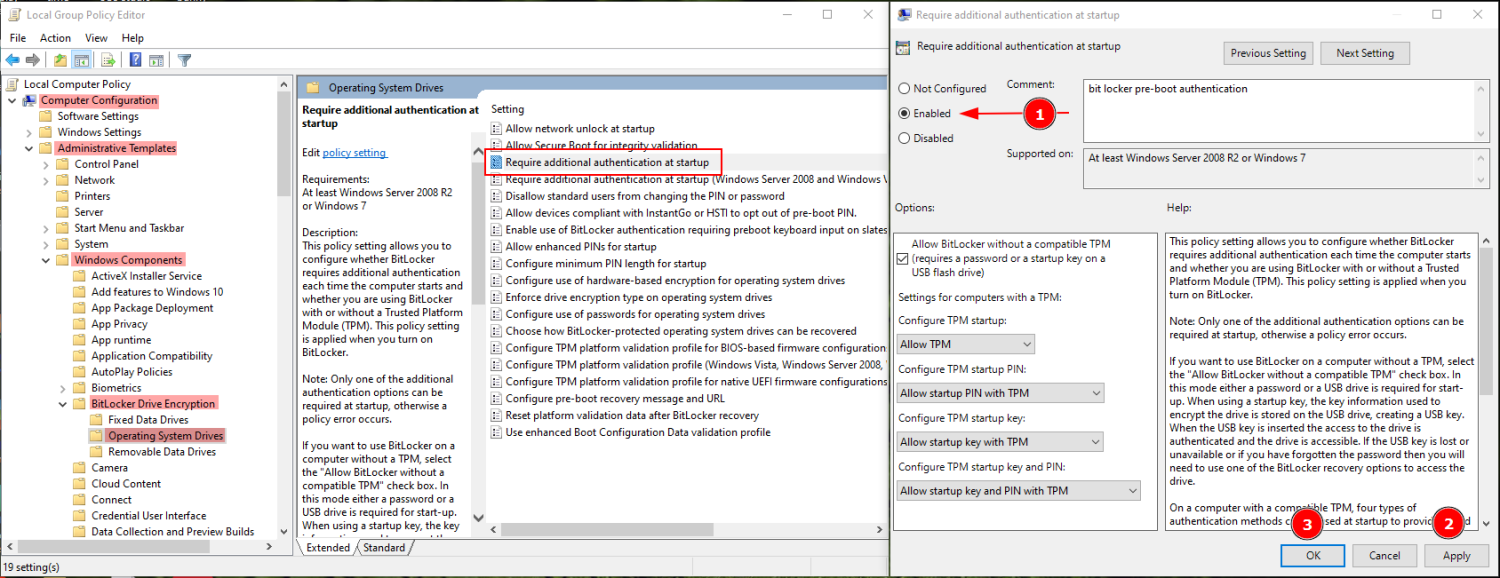
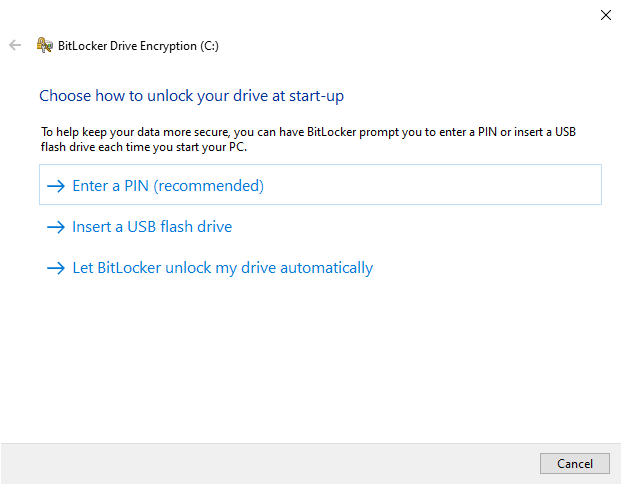
This, by default, uses the TPM security chip (version 1.2 or later) for authentication. And the machine boots up once the TPM returns the key. In such cases, there is no pre-boot authentication and anyone having your PC can turn it on by brute forcing through the Windows log-on password. However, one can turn on the pre-boot PIN from the local group policy editor to enjoy maximum security. Afterward, the TPM chip will ask for the recovery key and the pin before letting the machine boot. The differentiator here is that these chips come with brute-force protections. So, the attacker will have only a handful of tries before giving up. Just remember to configure this before initiating encryption. The process is simple enough. First, open Windows Run by pressing ⊞+R, type gpedit.msc, and hit enter. Then navigate to Computer Configuration > Administrative Templates > Windows Components > BitLocker Device Encryption > Operating System Drives: Now the BitLocker Encryption will need a PIN or a pre-set USB drive as a physical authentication before booting. Next, you progress to Encrypt entire drive or the used disk space only. Encrypting everything is generally the better idea for older computers since you may have data that can be retrieved from the empty sectors using Windows data recovery tools. Subsequently, you decide between using New encryption or a compatible mode. You can choose the New encryption mode since this is an operating system drive. The compatible mode would be more suitable for portable drives. Finally, it’s recommended to Run BitLocker system check on the following window to see if everything works perfectly.
BitLocker on Fixed Data Drives
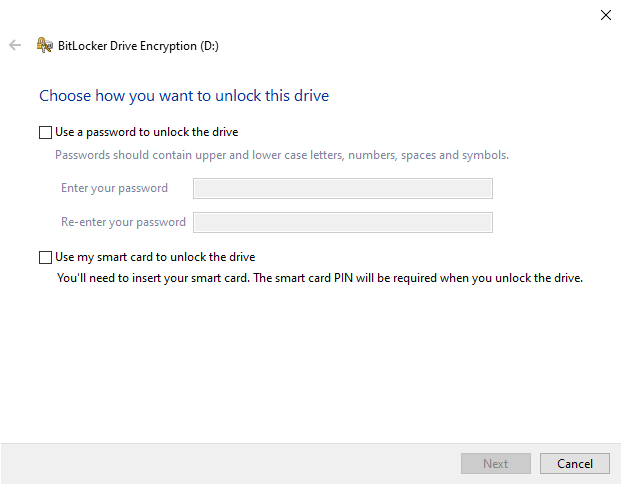
Encrypting these partitions and drives is more straightforward. This will ask you to set a password upfront. Once you get over this, the process is similar to encrypting operating system drives barring the BitLocker system checks. While BitLocker is handy, it’s unavailable to people using Windows Home variants. The second best free option is Windows Device Encryption, if your device supports it. This is different from the BitLocker in that it mandates TPM requirements. Besides, there is no means of pre-boot authentication. You can check the availability with System Information. Open Windows Run, type msinfo32, and press enter. Scroll down to the bottom and validate if Meet prerequisites are mentioned against Device Encryption Support. If it isn’t, most probably your device won’t support Device Encryption. However, you can contact manufacturer support to see for possible resolution. Alternatively, there are a few full disk encryption tools, free and paid, that you can use.
VeraCrypt
VeraCrypt is free, open-source encryption software for Windows, Mac, and Linux. Similar to BitLocker, you can encrypt system drives, fixed data drives, and portable drives. This is more flexible and gives many options for encryption algorithms. Besides, it can also encrypt on the fly. So, create an encrypted container and transfer your files to encrypt them. Additionally, VeraCrypt can create encrypted hidden volumes and supports pre-boot authentication like BitLocker. However, the user interface may be overwhelming, but nothing that a YouTube tutorial can’t sort out.
BestCrypt
You can call BestCrypt a user-friendly and paid version of Veracrypt. This gives you access to various algorithms and a host of options to achieve full disk encryption. It supports creating encrypting containers and system drives. Besides, you can deploy a password-approved booting. BestCrypt is a multi-platform encryption tool and comes with a 21-days free trial.
Commercial BitLocker Alternatives
These consist of enterprise-ready solutions based on volume licensing.
ESET
ESET full disk encryption is excellent for remote management. It gives you flexibility with on-premise and cloud encryption solutions. This features safeguarding hard drives, portable drives, emails, etc., with the industry-standard 256-bit AES encryption. In addition, this lets you encrypt individual files using File Level Encryption (FLE). You can check this out with the interactive demo or a 30-day free trial for a full-blown hands-on.
Symantec
Symantec, by Broadcom, is another leading player in providing enterprise-grade encryption facilities. This full disk encryption supports TPM ensuring the tamper-free state of institutional devices. Moreover, you get pre-boot checks, email, and removable disk encryption. Symantec helps you set single sign-on and can also protect cloud-based applications. This supports smart cards and has various recovery methods if the user forgets the passcode. Additionally, Symantec comes with file-level encryption, a sensitive file monitor, and various other features making it an irresistible end-to-end encryption solution.
ZENworks
ZENworks from Microfocus is the simplest way of handling AES-256 encryption in any organization. This supports an optional pre-boot authentication with username & password or a smart card with a PIN. ZENworks features centralized key management to help users stuck at boot logins. You can make encryption policies for devices and enforce them over a standard HTTP web connection. Finally, you can avail of its free, no-credit card trial to see it firsthand.
FDE vs FLE
Sometimes it’s not worth encrypting an entire disk. In such cases, it’s wise to protect a specific file giving birth to File Level Encryption or File Based Encryption (FBE). FLE is more common, and we often use it without acknowledging its presence. For instance, WhatsApp conversations are end-to-end encrypted. Similarly, emails sent via Proton mail are also automatically encrypted and only the recipient can access the contents. In a similar fashion, one can protect a file with FLE with tools such as AxCrypt or FolderLock. A distinct advantage of FBE over FDE is that all files can have different encryption keys. Ergo, if one gets compromised, the others will remain safe. However, this brings in the additional hassle of managing such keys.
Conclusion
Full Disk Encryption is crucial when you lose a device containing sensitive information. While every user has some crucial data onboard, it’s the businesses that need disk encryption more than anyone else. Personally, BitLocker is the best encryption tool for Windows users. VeraCrypt is another option for someone who can endure a dated interface. And the organizations shouldn’t rely on someone’s verdict but take the trials to choose the best for their use case. The only thing a business owner should avoid is vendor locks. PS: Check out our encryption vs authentication software to brush up on the basics.

![]()