SQLi (SQL Injection) is an old technique where hacker executes the malicious SQL statements to take over the website. It is considered as high severity vulnerability, and the latest report by Acunetix shows 8% of the scanned target was vulnerable from it. Since SQL (Structured query language) database is supported by many web platforms (PHP, WordPress, Joomla, Java, etc.), It could potentially target a large number of websites. So you see, it’s essential to ensure your online business website is not vulnerable to SQLi, and the following will help you to find if any. Note: Performing SQL injection generates high network bandwidth and sends a lot of data. So, ensure you are the owner of the website you are testing.
suIP.biz
Detecting SQL Injection flaws online by suIP.biz support MySQL, Oracle, PostgreSQL, Microsoft SQL, IBM DB2, Firebird, Sybase, etc. database. SQLMap powers it so it will test against all six injection techniques.
SQL Injection Test Online
Another online tool by Hacker Target based on SQLMap to find bind & error based vulnerability against HTTP GET request.
Invicti
An enterprise-ready comprehensive web security scanner – Invicti does more than just the SQL vulnerability test. You can integrate with SDLC to automate web security. Check out this vulnerability index, which is covered by the Invicti scan.
Vega
Vega is an open-source security scanner software that can be installed on Linux, OS X, and Windows. Vega is written in Java, and it is GUI based. Not just SQLi, but you can use Vega to test many other vulnerabilities such as:
XML /Shell/URL injectionDirectory listingRemote file includesXSSAnd much more…
Vega looks promising FREE web security scanner.
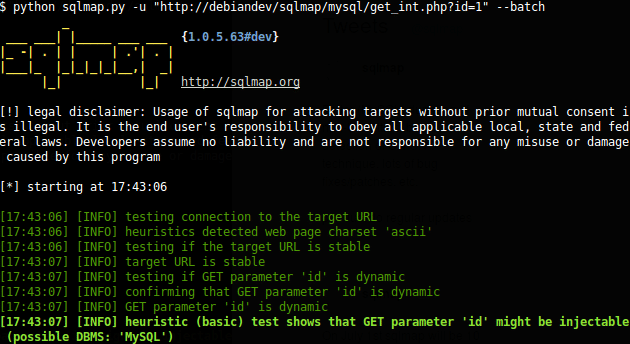
SQLMap
SQLMap is one of the popular open-source testing tools to perform SQL injection against a relational database management system. Sqlmap enumerates users, passwords, hashes, roles, databases, tables, columns, and support to dump database tables entirely. SQLMap is also available on Kali Linux. You can refer to this guide to install Kali Linux on VMWare Fusion.
SQL Injection Scanner
An online scanner by Pentest-Tools test using OWASP ZAP. There are two options – light (FREE) and full (need to be registered).
Appspider
Appspider by Rapid7 is a dynamic application security testing solution to crawl and test a web application for more than 95 types of attack. The unique feature by Appspider called vulnerability validator lets the developer reproduce the vulnerability in real-time. This becomes handy when you have remediated the vulnerability and would like to re-test to ensure the risk is fixed.
Acunetix
Acunetix is an enterprise-ready web application vulnerability scanner, trusted by more than 4000 brands worldwide. Not just the SQLi scan, but the tool is capable of finding more than 6000 vulnerabilities. Each finding is classified with potential fixes, so you know what to do to get it fixed. Further, you can integrate with CI/CD system and SDLC, so every security risk is identified and fixed before the application is deployed to production.
Wapiti
Wapiti is a python-based black-box vulnerability scanner. It supports a large number of attack detection.
SQLi and XPathCRLS and XSSShellshockFile disclosureServer-side request forgeryCommand execution
and more.. It supports HTTP/HTTPS endpoint, multiple authentication types like Basic, Digest, NTLM, and Kerberos. You have an option to generate scan reports in HTML, XML, JSON, and TXT format.
Scant3r
A docker ready, scant3r is a lightweight scanner based on Python. It looks for potential XSS, SQLi, RCE, SSTI from headers and URL parameters.
What’s next?
The above tools will test and let you know if your website has SQL injection vulnerability. If you are wondering how to protect your site against SQL injection, then the following will give you an idea. The poorly coded web application is often responsible for SQL injection, so you got to fix the vulnerable code. However, another thing you can do is to implement the WAF (web application firewall) in front of the application. There are two possible ways to integrate WAF with your application.
Integrate WAF in Web Server – you can use WAF like ModSecurity with Nginx, Apache, or WebKnight with IIS. This would be possible when you are hosting your website on your own, like in Cloud/VPS or dedicated. However, if you are on shared hosting, then you can’t install it there.Use cloud-based WAF – probably, the easiest way to add site protection is by implementing the website firewall. The good thing is it will work for any website, and you can get it started in less than 10 minutes.
If you are curious to learn about SQL Injection, then check out the following resources.
CheatsheetBasics
Next, check out how to find security risks in NoSQL databases.

![]()