Not only do you need to make sure your web applications are secure for regulatory reasons, but you (should) also care about your client’s data and the risk exposure to your company. You certainly have plenty of options when it comes to securing your web applications, all with their pros and cons. Some solutions rely on identifying security issues in the source code of your applications. Others protect your applications against attacks. And others rely on dynamically testing your web applications’ security at runtime, just like a hacker would do. The focus of this article is on this latter case, namely on Probely. What makes Probely interesting when compared to others is that it tackles two of the main issues of web vulnerability scanners: the scanning coverage of modern web applications and the quality of the results. Probely has two different editions: a self-serviced one targeted at SMBs and another targeted at Enterprises or companies with many web applications and APIs. Probely focuses on providing exceptional coverage across modern development environments and eliminating false positives with Evidence-Based Scanning results while allowing you to integrate DAST scanning into your development life-cycle. Too good to be true? Read on to learn about my analysis of Probely.
What exactly does Probely do?
With developers and every business size in mind, Probely tests your applications and APIs, scanning them to find security issues and vulnerabilities. When the testing is completed, it provides guidance on how to fix the issues found. Your developers and security engineers can work with Probely through its intuitive user interface. But if you need power and flexibility, you can rely on their full-featured API since they follow an API-first development approach. Their API provides all features that you see on the user interface, allowing you to integrate Probely into a CI/CD pipeline, vulnerability management tool, orchestrator, or issue tracker. If you use the popular ones, you might have an out of the box integration. That is the case for tools such as JIRA, Jenkins, Azure DevOps, DefectDojo, CircleCI, and Slack. But if you developed your own issue tracker or orchestrator, then the API is the way to go.
Coverage, Crawling, and Accuracy
Probely uses a next-generation spider to navigate rich Javascripts applications the same way a normal browser would, resulting in excellent coverage of the site, which is a problem for many other DAST tools. This spider is ideal for Single-Page Apps, such as those based on React or Angular JS. Keep in mind that a scanner can only identify vulnerabilities in pages that were found. Therefore a good spider is of the utmost importance. Probely also offers different scanning profiles, depending on which environment you want to test. You can set a lesser intrusive scanning profile if you would like to scan your production environment. If you are testing your QA environment, you can set a more thorough profile for more complete scans. By testing a pre-production environment, you can identify and fix vulnerabilities before deploying the application in production.
Reporting
Although Probely detects an extensive list of vulnerabilities, it focuses on reporting what is relevant and without false positives. For certain classes of vulnerabilities, it provides evidence that the vulnerability is real, saving your team’s time in validating if vulnerabilities are real and relevant. Probely provides extensive reporting from the interface, but it can also sync vulnerability information with an issue tracker or vulnerability management tool, allowing you to fit Probely into your existing security and development workflows. Probely can test your software against vulnerabilities such as those listed in the OWASP TOP 10 and much more. It can also help you achieve compliance by checking specific requirements of PCI-DSS, GDPR, HIPAA, and ISO270-01.
Taken from the OWASP TOP 10 report, you’ll have at a glance what’s wrong regarding this compliance.
Interface
The interface is simple and easy to navigate, allowing you to get up and running quickly. The Enterprise edition allows you to control users, roles, and set custom roles. You can also use labels to organize users, assets, and vulnerabilities to manage your web application security better. Since all features are available through the API, you can easily integrate Probely into your other enterprise security applications and processes. If you use Jira or Azure Boards, you can configure Probely to automatically send all vulnerabilities to your issue tracker. When the developer fixes and closes the issue on the issue tracker, it will automatically trigger a re-test on Probely, which will check if the vulnerability is properly fixed. If it isn’t, the issue is reopened on the issue tracker. This allows your development team to handle a vulnerability report like any other bug, directly on the issue tracker, without even using Probely’s interface. Nice, huh? 🙂
Getting started 🚀
For my testing purposes, I was using Probely’s Enterprise edition. They also offer a standard edition and different plans to choose from, including a free plan. In the free plan, the scan only tests three classes of vulnerabilities: cookies flags, security headers, and SSL/TLS issues. The Pro plan offers most of the features and focuses on SMBs and organizations having five or fewer targets to scan. The Enterprise edition focuses on organizations that have a large number of targets and includes additional features such as those that are common in enterprise software: users, groups, roles, and permissions. It also allows you to scan internal targets (on your private network) by installing an agent that is provided.
Adding a target
Adding a target is easy. Once you log in with your account, you need to navigate to the Targets page and click on Add. Then you provide a name, a URL, and one or more labels — i.e., Testing, Production, Development, etc. — for the new target. To let Probely scan this target as a standalone API without a supporting web app, you should check the corresponding option to identify it as an API target.
If your target is not exposed on the Internet and you installed a Probely agent on your private network, you can select which agent to use while adding a target. After adding a target, you need to validate its ownership because Probely needs evidence that you have the necessary privileges to run a scan on it. There are two alternative methods to validate the target: loading a file with provided content on the target’s root or adding a TXT entry to your DNS record, with the domain’s name and some specific record content. Once the target is validated, you are ready to scan it just by pressing the Scan button. You can check a scan’s progress and status by navigating to the Scans tab on Probely’s dashboard. This page will show you when the scan started and what it found so far. Findings are colored by severity, so you can see at a glance if there are critical issues that need to be addressed immediately. If your website has a login page and you want Probely to perform a scan behind it, you must provide credentials that allow it to crawl the site as an authenticated user. Probely supports most authentication methods for login pages.
Scanning an API
To scan an API target, Probely needs you to provide its schema. You do this when you add an API target, either by providing the OpenAPI schema URL or by uploading the schema if you previously saved it as a local file. The URL option lets Probely fetch the schema before every scan, ensuring it always works with the latest version of your schema.
There are also different options in terms of authentication methods for API access. Probely supports not only static tokens but also allows dynamic authentication configuration when scanning APIs. You can configure a login endpoint where Probely can get an authentication token, or you can set a custom header with a fixed API key in it. You can also provide custom parameter values that Probely will use for those found in the schema. Once you finish configuring the API authentication and parameters, you can start the scan by pressing the Scan Now button. After a few seconds, you will be able to follow the scan progress on the same Scan page. When the scan ends, you can download a coverage report that shows all endpoints found and each response code. This report will also tell if there were failing endpoints.
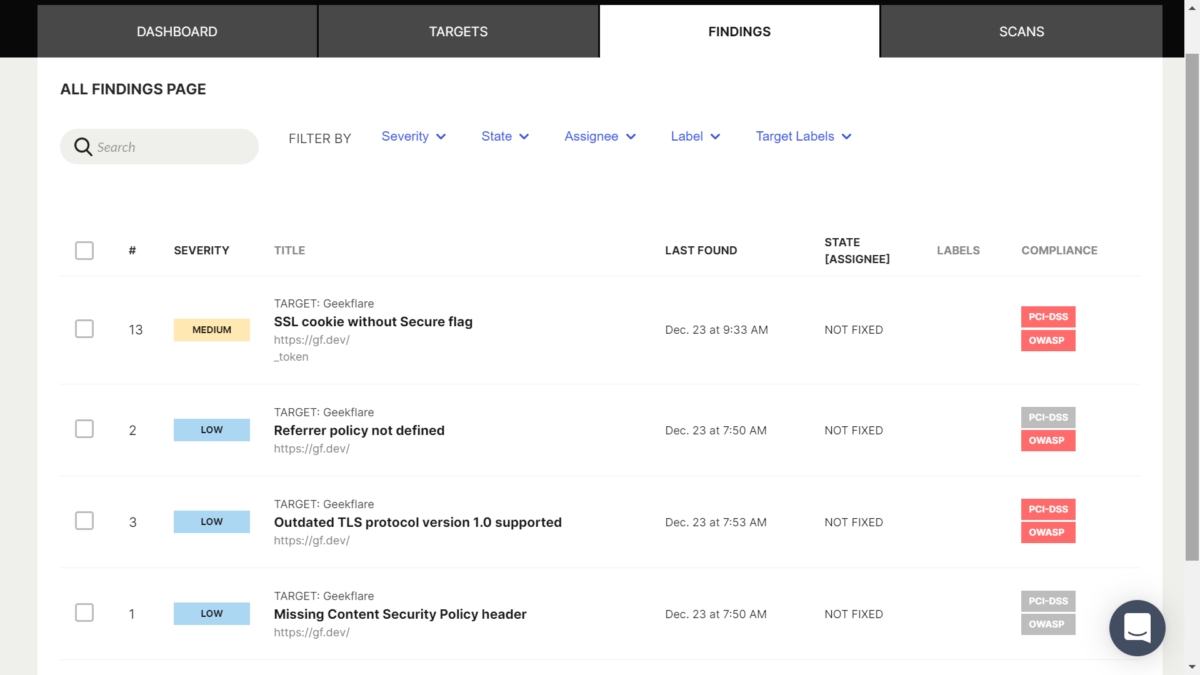
Checking your findings
The findings page shows the scan results as soon as they are found, even when scans are in progress. Each finding shows a severity (high, medium, or low), the corresponding target and URL, the finding description, the time and date when it was found, its state (fixed or not fixed) and assignee, and whether it affects PCI-DSS or OWASP compliance.
Besides keeping you informed about the detected vulnerabilities, the findings page is also useful to assign vulnerabilities to your team to fix. To do so, you click on the checkbox on the left and select the assignee from a dropdown menu. Probely also provides information on how to fix the vulnerabilities that have been found. Along with these instructions, you can see the full request and response, and the evidence.
On the Dashboard page, you can see various charts that summarize the scanned targets’ security risk. The graphs show trends in different interesting metrics, such as risk scores, the average time to fix issues, and severity levels. You can also glance at the sites that require the most attention and a top 5 ranking of vulnerabilities with the highest incidence.
Finally, on the Integrations page, you can configure Probely to integrate with many different tools to manage projects, team communication, issue tracking, and more. The available integrations include Azure Boards, DefectDojo, Slack, Jira, Jenkins, and CircleCI.
A tool for developers and security teams
For agile development teams, time-to-market is a top priority. Whatever you can do to minimize the time it takes for your software to go into production without compromising quality is highly welcome. Probely offers just that – a cost-effective way to improve the security of your websites and APIs, helping you keep your schedule-related promises and deliver high-quality software products. For security teams, Probely provides you with a platform to secure your web applications and manage the vulnerabilities that require remediation. It also allows you to offload some of the security testings directly to development teams while having a supervision role. Probely offers free trials, enterprise evaluation licenses, and product demos. Contact Probely to get started.

![]()